- Trust Center
- Security
Security
- Administrative Controls
- Technical and Organizational Measures
- Vulnerability Disclosures
- Alerts and Updates

Attestation and Compliance
We are committed to maintaining the highest standards of administrative and technical control. Service Organization Control (SOC) 2 report documents demonstrate that an independent accounting and auditing firm examined an organization’s control objectives and activities and tested those controls to ensure that they are operating effectively.
SOC 2 is a technical auditing process conducted by an independent accounting and auditing firm to measure the security of an organization’s unique data processing systems. SOC 2 provides a neutral determination regarding whether effective safeguards and controls are in place. Our SOC 2 reports verify the existence of internal controls that have been designed and implemented to meet the AICPA Trust Services Criteria for security.
You can obtain copies of our product-specific SOC reports and other security documentation by visiting our Product Security Profiles.
Background Checks
We perform background screening on all team members to the extent possible within local law. Team members also sign nondisclosure agreements. Additionally, all team members annually affirm their compliance with the company handbook, data privacy, and security policies.
Awareness and Education Program
Upon joining and at least annually thereafter, all tax.com team members undergo tested security training. This training covers safe handling and classification of data, compliance, security best practices, and adherence to the principle of least privilege. Regular training and testing on phishing are provided through an internal mock phishing program, which includes reinforcement training for underperformance.
Upon joining and at least annually thereafter, all tax.com team members undergo tested privacy training covering topics such as personal data, personally identifiable information, and sensitive personal information as regulated by various applicable privacy laws (specifically including the General Data Protection Regulation [GDPR] and California privacy laws).
Specific tax.com team members receive additional role-based training. For example, the tax.com software engineering team receives training on how to identify the latest threats and use secure coding techniques to build resilient and secure solutions, with special emphasis on privacy by design and secure software development.
Incident Management
Tax.com platform security is overseen by a Cyber Security team led by a Chief Information Security Officer (CISO). The Cyber Security team maintains an Incident Response Plan (IRP) that addresses the segregation of duties, details the processes for detecting, reporting, identifying, analyzing, and responding to security incidents impacting firm infrastructure and data under its custody and control, and provides for post-event analysis to identify and capture any lessons learned.
Data Breach Notification
In the event of a data breach, we will follow its IRP and contractual obligations to notify partners and customers of incidents impacting the infrastructure and data related to the delivery of their services and products.
Vendor Management
We may engage subprocessors to perform or deliver services. In such cases, we only grant these subprocessors access to customer data as required to perform their services. These subprocessors are bound by written agreements that impose strict data protection measures mandated by tax.com and applicable regulations. The tax.com written agreements with subprocessors ensure that the level of data protection provided is no less stringent than the level of data protection specified in the customer’s agreement with tax.com.
Furthermore, we subject certain vendors to vendor assessments to verify the implementation of proper data security and privacy practices throughout the vendor relationship. Any changes to vendor services or existing contracts undergo a security risk assessment to ensure that they do not introduce additional or undue risk.
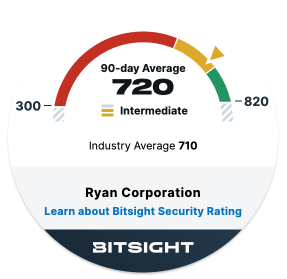
Security Rating
The BitSight Security Rating is an independent, data-driven assessment of cybersecurity readiness.
BitSight is the most widely adopted Security Ratings solution for all industries and markets, and is trusted by 20% of Fortune 1000 companies, the Big 4 accounting firms, and numerous global insurance companies.
Additional information on Security Ratings may be found at BitSight’s website.
Data Center
We store critical client information in high-security data centers, including cloud storage providers. Data center security includes physical security measures designed to minimize disruption and prevent theft, tampering, and damage, including:
- 24×7 monitoring
- Cameras
- Visitor logs
- Entry requirements
- Climate control
- Fire detection and suppression systems
- Dedicated cages to separate our equipment from other tenants in the data center
Data Encryption
Our internet-accessible systems have Transport Layer Security (TLS) enabled to encrypt customer traffic by default. Our web application endpoints use TLS for secure transport.
Upon joining and at least annually thereafter, all tax.com team members undergo tested privacy training covering topics such as personal data, personally identifiable information, and sensitive personal information as regulated by various applicable privacy laws (specifically including the General Data Protection Regulation [GDPR] and California privacy laws).
Specific tax.com team members receive additional role-based training. For example, the tax.com software engineering team receives training on how to identify the latest threats and use secure coding techniques to build resilient and secure solutions, with special emphasis on privacy by design and secure software development.
Customer Data Protection and Records Management Policy
We maintain an internal Customer Data Privacy policy governing the proper use and protection of customer data. We further maintain an internal Record Retention and Disposal policy developed in view of industry-standard compliance requirements such as the GDPR. Where appropriate, platforms use built-in rules to govern retention and tax.com team members follow operational guidelines for the deletion of data upon termination of services. When deleted, Customer data solutions is irrevocably logically and physically deleted according to the protocols of best-in-class hosting services providers.
Availability Control, Backup, and Recovery
We use best-in-class hosting services providers with resilient and redundant systems to enable automated failover capability. Our framework focuses on three core elements:
- People: We maintain policies and procedures for Incident Response and trains its information security on these documents.
- Processes: We maintain a program for business continuity to sustain certain operations during a significant business disruption.
- Technology: We use a prioritized approach to restoring essential information technology infrastructure, hardware, and software during a business continuity event.
We perform regular and secure backup and recovery testing of data and supporting systems. The intervals for backups depend on the type of data and underlying repositories, ranging from minutes to daily.
Intrusion and Malware Protection
We employ a robust, multilayer defense-in-depth strategy for safeguarding against intrusions and malware. The security architecture is designed to centrally manage and monitor the protection of both company assets and client data. Furthermore, we require vendors determined to be “high risk” to complete vendor assessments to verify the implementation of proper data security and privacy practices throughout the vendor relationship. Any changes to vendor services or existing contracts undergo a security risk assessment to ensure that they do not introduce additional or undue risk.
Logging and Monitoring
We employ processes to log, monitor, and respond to events and anomalies in its systems and solutions. We use centralized non-repudiable logging and monitoring solutions to identify and investigate possible security events and track anomalous behavior. Dedicated and centralized Security Info and Event Management (SIEM) tools allow us to proactively model risks and respond to incidents.
Identity and Access Control
We limit access to customer data to authorized team members with login credentials. Security is enhanced through multi-factor authentication (MFA), single sign-On, need-to-know / least-privilege principles, and restricted administrative account access. Strong password controls enforce length, complexity, and 90-day expiration, with limited reuse. To strengthen security, we implement session expiration, terminating inactive sessions to prevent unauthorized access. Failed login attempts result in account lockouts to thwart brute-force attacks. Regular access reviews are conducted to help ensure access privileges remain appropriate and up to date. Lastly, we promptly revoke access upon employee termination, further preventing unauthorized data access.
Secure Design Reviews and Threat Modeling
We employ a secure software development methodology that incorporates security throughout the systems development lifecycle in connection with the development and maintenance of its information systems. Minimally, applications have controls to protect against known vulnerabilities and threats, and secure coding standards are employed that comply with industry standards such as OWASP.
Patching
We maintain a proactive approach to safeguarding customer information through regular and timely patching of our software and infrastructure, keeping potential vulnerabilities at bay and providing customers with a safe and reliable platform.
Penetration Testing
We regularly contract with third parties to simulate attacks against many of our solutions to identify potential points of weakness or vulnerability.
Vulnerability Disclosure Program
We participate in a bug bounty program to incentivize responsible reporting of bugs in tax.com applications.
Frameworks
We align our controls framework to NIST standards.
Vulnerability Disclosure Program
Responsible Disclosure
We are committed to maintaining the confidentiality, integrity, and availability of the systems and information in our control. If you detect an information security issue in any of our systems while using www.tax.com or a Ryan application, we strongly urge you to report it using our Vulnerability Disclosure Program form below.
We aim to rapidly address any security issues while minimizing the negative impact on our customers. To achieve this, we ask that you provide the information necessary to understand the issue fully.
Upon validation of the issue, we will categorize the issue’s priority based on our assessment. For transparency, we will strive to provide regular updates on the issue’s status, where feasible. If we identify the issue as a false positive or an issue we’re already aware of, we will inform you of this fact.
To help expedite the process, we ask that you please provide screen captures of the issue and respond promptly when we seek your clarification or input.
Please also include any relevant technical details, such as:
- The URL where the issue occurs
- The ID used to log in
- The time of day you discovered the issue
- Your source IP
The form below is the only way to submit findings. Please do not contact us directly with findings, as these requests will be ignored.
Table of contents:
Compliance
If you have acted in a way that may harm our customers, our software products, our associates, or our vendors, we consider this a breach of our Terms of Use. Publicly disclosing an information security issue (for example, methodologies or codes) in a public forum (such as on social media, in a chat room, or with friends) is also a breach of our Terms of Use, as would be the creation of any fraudulent accounts.
Ryan, LLC has received multiple requests for information pertaining to the MOVEit Transfer Software vulnerability. Ryan as an organization does not utilize the affected version of the MOVEit Transfer Software in the ordinary course of business. None of Ryan’s licensed software products utilize MOVEit Transfer Software, and Ryan’s service delivery team does not use MOVEit in ordinary practice. Regarding third-party service providers, Ryan is taking a proactive stance and is contacting third parties regarding this issue and is seeking to ensure timely remediation where necessary.
On Friday, December 10, 2021, we were made aware of a vulnerability in the Log4j logging framework, CVE-2021-44228. We immediately initiated our incident response process to determine our usage of this framework and its impact across our products and our infrastructure.
For affected systems, we’re monitoring telemetry and have not detected any successful exploitation at this time. We’re applying the recommended solutions by the Apache Software Foundation and, when applicable, patching our systems with the latest version of Log4j. We continue to actively monitor the situation for any new developments. No action by users of our products is required in order to continue safely using the solution.